ZTNA can incorporate additional factors like endpoint security into access decisions, preventing connections from unauthorized devices. It can also make network infrastructure invisible, reducing the risk of threats that might otherwise infect user devices. ZTNA solutions can be implemented as a gateway solution or provided as a service through a provider. The former offers granularity, customization, and integration with existing systems. The latter offers simplicity, scalability, and ease of deployment.
Table of Contents
Zero Trust Architecture
Keeping up with the many technologies, strategies, and policies thrown around in the cybersecurity industry can take time and effort. ZTNA solutions, sometimes called software-defined perimeter (SDP), is one of these emerging technologies rapidly gaining popularity. A Zero Trust architecture addresses lateral threat movement by combining micro-segmentation with granular perimeter enforcement based on data, user, and location. It also enables continuous verification by authenticating users and continuously verifying access to applications, devices, infrastructure, services, and cloud workloads – based on risk-based multi-factor authentication, identity protection and validation, next-generation endpoint security, and the secure management of email, encryption, and end-to-end traffic inspection. The first step to implementing a zero-trust solution is identifying critical processes and evaluating their risks. This includes understanding which applications are being used, when, how they are accessed, and the data sensitivity involved. Once identified, these business processes should inform a security policy that dynamically evaluates and enforces an organization’s security posture.
Perimeters
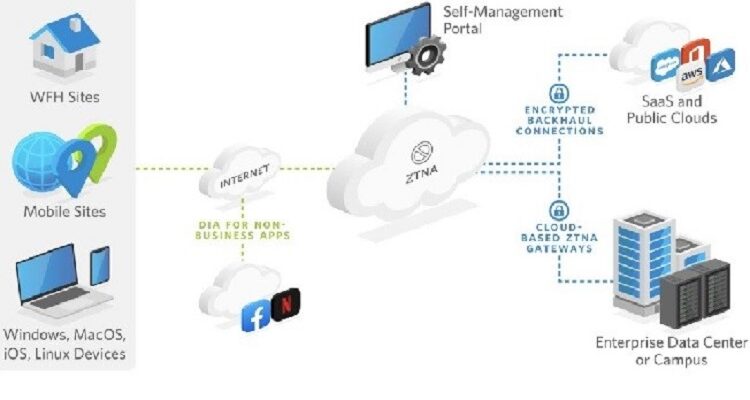
Zero trust networks require access to data and applications to be verified before any network access. It is a security model that replaces traditional VPNs with micro-perimeter gateways and authentication protocols that continuously evaluate users, devices, and the data used based on context and reassess their posture. This eliminates implicit trust and enables secure, direct connections to apps and resources within the cloud or data center without a VPN. The core principle of Zero Trust is “never trust, always verify.” Enterprises must inventory all services, privileged accounts, and user identities to implement this. They must establish policies based on granular contextual information, including device, location, time of day, the type of data being used, and the requested application. The resulting policies must be adaptive to ensure that access privileges are continually reassessed.
Connectivity
Zero Trust connectivity solutions can strengthen network security in the cloud and enable an actual anywhere-work environment. By replacing VPNs with a distributed Zero Trust model that uses micro-segmentation, phish-proof MFA, and an edge compute point of presence solution to reduce the impact on network performance, it can be easier to secure access to critical applications for both remote and local employees. Unlike the perimeter-based approach of traditional VPNs, Zero Trust architecture assumes that everything outside the firewall is hostile by default. This enables continuous authentication to ensure that only authenticated and trusted devices, users, and apps can access your data. In addition, you can monitor and detect risks from a centralized dashboard to ensure your cybersecurity controls are functioning correctly. The user trust pillar includes password authentication, multi-factor authentication, and dynamic scoring, all designed to ensure that the correct person is connecting to your systems. The device trust pillar includes identity and posture, compliance, device management, and software-defined security to ensure that only authorized devices are allowed into your network. Finally, the data pillar includes encryption, granular policy and access control, and visibility to ensure that only legitimate communication occurs between your systems. Additionally, data is categorized based on mission criticality and isolated from those that do not need it. The goal is to protect all data, workflows, and services regardless of network location.
Access Control
Zero trust network access solutions can help protect organizations from advanced cyber threats, data breaches, and other vulnerabilities by limiting the attack surface. This is possible by restricting access to apps and other resources based on authenticated devices, users, and location, thereby eliminating the risk of lateral movement of threats across the corporate network. ZTNA security solutions can also prevent the proliferation of IoT devices and other malware in the workplace by requiring authentication and authorization procedures for BYOD and other personal devices that need to access applications. These solutions can also limit access to privileged accounts by requiring rigorous authentication and multi-factor security. When implementing ZTNA, businesses should choose a solution that provides granular controls through a centralized admin portal and offers complete security features, including real-time verification. Authentication policies can be configured for user groups, individual users, and context-aware parameters such as device posture, geographic location, or time of day. Another feature to look for is a centralized console that can easily integrate with the identity-provider solutions an organization already has in place. Additionally, businesses should consider deploying a cloud-based or managed zero-trust security solution to reduce the complexity and cost of deployment and infrastructure. This allows for fast and easy scaling of capacity while minimizing the company’s reliance on external vendors, which can potentially expose sensitive data or be subject to outages.












Comments